Don't miss the blind spots: API monitoring for digital resilience

In today's digital world, applications are the lifeline of businesses. They're the engines powering everything from e-commerce transactions (think adding items to your shopping cart) to internal communication tools (imagine sending a message to a colleague). Any glitch or outage in these applications can have a domino effect, impacting revenue, productivity, and even brand reputation.
The invisible threads between these applications that enable them to transfer data and functionality efficiently are application programming interfaces (APIs). While APIs are designed for resilience, just like any complex system, they are not immune to issues. That's where API monitoring comes in—it sheds light on potential issues and ensures your applications keep running smoothly.
Beyond the surface: Unveiling the hidden layers of API transactions
APIs power seamless interactions between applications, enabling data exchange and functionality sharing. But what happens beneath the surface of a simple API call? Let's delve into the various steps that orchestrate every API transaction, ensuring smooth and secure communication.
- The request layer: Setting the stage
The journey begins with a request. Your application initiates the process by sending a well-defined message to the target API. This message specifies the desired action (like fetching data or performing an operation) and includes any necessary data (like user credentials or search parameters). Think of it as sending a carefully worded letter outlining your request. - Authentication checkpoint: Verifying identities
Before granting access, the API acts like a security guard, verifying the legitimacy of the request. This is often done through authentication mechanisms like tokens or API keys. Imagine the security guard checking your ID before allowing you to enter a building. - Authorization check: Are you allowed in?
Even with valid identification, not everyone gets full access. The API implements authorization checks to determine if the requesting application has the necessary permissions to perform the requested action. Think of it as having the proper access card to enter a specific restricted area within the building. - Routing the request: Finding the right department Once authenticated and authorized, the request is routed to the appropriate internal service within the API. This service might be a database, a processing engine, or another API altogether. Imagine the security guard directing you to the specific department that can handle your request.
- Processing the request: Fulfilling your needs
The designated service springs into action, processing the request based on its specifications. This can be processes like obtaining data from a database, calculations, or triggering actions in other platforms. Think of the department working on your request, retrieving files, or completing the task you outlined in your letter. - Response formulation: Sending back the answer
The service crafts a response message tailored to the initial request. This response might contain the requested data, confirmation of a successful operation, or an error message if something went wrong. Imagine the department sending back a response letter with the information you requested or informing you of any issues. - Response delivery: Back to the sender
The API carefully packages the response message and sends it back to the application that initiated the request. This ensures your application receives the necessary feedback to proceed with its tasks. Think of the response letter being delivered back to you. - Security throughout: Safeguarding the journey
Security measures are woven throughout the entire process. Encryption protects sensitive data during transmission and logging tracks activity for audit purposes. Imagine secure protocols being used throughout the interaction and a record being kept of the entire process. Understanding these hidden layers empowers developers and businesses to build robust and secure API ecosystems. By appreciating the intricate dance behind every API transaction, we can ensure seamless communication, efficient data exchange, and a thriving digital landscape.
The domino effect of API failures: Ensuring digital resilience
APIs can bring a company's operations to a screeching halt when they fail. Imagine a travel website relying on an API to fetch flight information. An API failure could cause a cascade of problems. Frustrated users might encounter error messages, outdated flight listings, or an inability to complete bookings, leading to lost revenue for the company.
The disruption extends beyond the customer experience. Internally, APIs are often integrated into critical business processes. A failing inventory management API could disrupt order fulfillment, impacting customer satisfaction. Similarly, a malfunctioning payment processing API could lead to failed transactions and lost sales.
Data becomes another casualty of API failures. When APIs fail, applications become isolated silos, unable to access or share data. This hinders collaboration and can stall critical business decisions. In the worst-case scenario, API failures can expose security vulnerabilities. If an API doesn't properly authenticate or authorize requests, hackers might exploit these gaps to gain unauthorized access to sensitive data.
The impact on users is equally significant. A failing API in a food delivery app could prevent users from placing orders or tracking their deliveries. The severity of the impact depends on the duration and nature of the outage. Frequent outages or security breaches can erode user trust and damage a company's reputation. Businesses heavily reliant on APIs for innovation might be hindered in launching new features or integrations if API failures become a recurring issue.
The good news is that API failures can be mitigated. By taking proactive measures like API monitoring, robust error handling, redundancy, strong security practices, and regular testing, businesses can build resilient APIs that ensure the smooth flow of data and functionality within their digital ecosystem, ultimately delivering a seamless and positive experience for users.
API failures can be mitigated, and these are some proactive measures businesses can take:
- API monitoring: Monitor API performance regularly to find plausible issues before they transform into outages.
- Robust error handling: Implement mechanisms within applications to gracefully handle API failures and provide informative error messages to users.
- Strong security measures: Implement robust authentication, request throttling, authorization, and encryption protocols to safeguard sensitive data transmitted through APIs.
Here's how API monitoring can prevent such nightmares and bolster your digital resilience
Monitoring tools track key API metrics like latency (how long it takes for an API to respond), error rates (the number of failed requests), and throughput (the volume of data flowing through the API). These metrics act as an early warning system, providing alerts if response times spike, error rates climb, or traffic surges unexpectedly. Patterns or trends can also be analyzed over a period of time using anomaly detection, and you can opt to get notified. For example, a sudden increase in error rates during a flash sale on your online store might indicate an API overload. Catching this issue early allows you to scale up your API infrastructure or implement temporary measures to handle the surge, preventing failures during customer checkout.
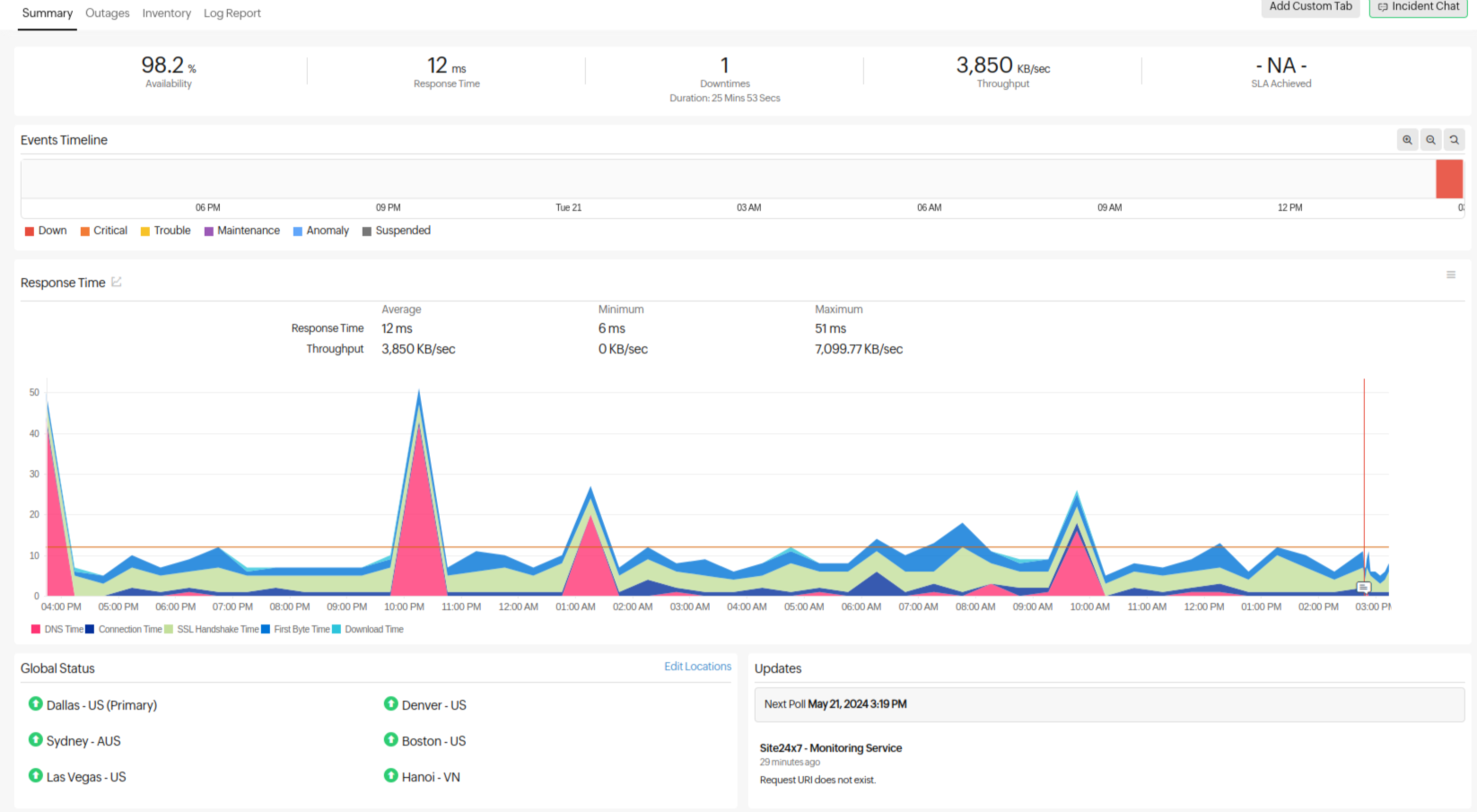
Monitoring also helps to identify bottlenecks and inefficiencies within your APIs. Analyzing performance data can help in identifying those areas that need improvement. For instance, monitoring might reveal that a specific API call consistently has high latency. By investigating the code or optimizing the database queries involved, you can streamline the API call and ensure faster data exchange between applications.
API monitoring tools can be your security superhero, and they can help in tracing any suspicious activity or access attempts.
When issues do arise, API monitoring tools provide valuable data to pinpoint the root cause quickly. This speeds up troubleshooting and minimizes downtime for your applications. For instance, if a specific API endpoint starts returning errors, you can analyze the error messages and logs within the monitoring tool to diagnose the problem. This targeted approach saves precious time compared to blindly searching for the issue within a large codebase.
API monitoring is no longer a luxury, but a necessity. It's the proactive approach that safeguards you from the unseen dangers lurking within your API infrastructure. By continuously monitoring your APIs, you can identify potential issues before they snowball into outages, disruptions, and lost revenue. Think of it as an investment in your digital future—a future where your applications function seamlessly, user trust remains strong, and innovation thrives. Embrace API monitoring and illuminate the path to a resilient and successful digital landscape.
Topic Participants
Bela Susan Thomas